What is the anatomy of a ransomware attack?
The hybrid workforce is here to stay. Here’s the good news: This new work style can keep employees happy, boost productivity, and reduce a range of costs, from real estate and travel to employee attrition.1
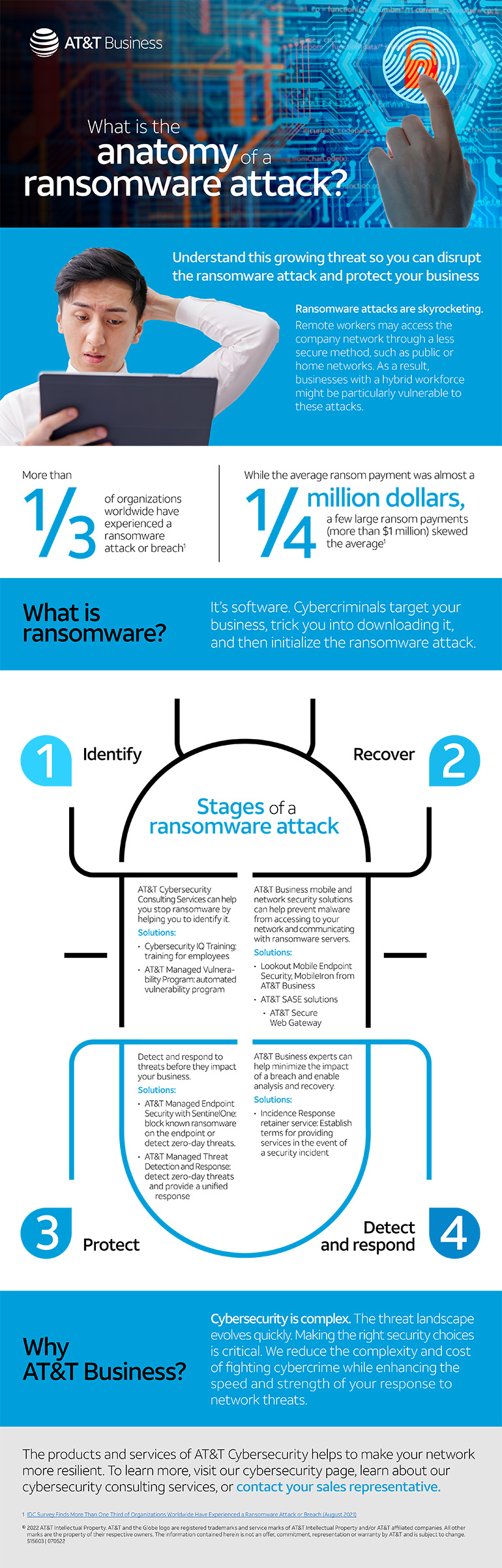
Now the bad news: Businesses with a hybrid workforce are particularly vulnerable to ransomware attacks. Many organizations that had to pivot quickly to work-from-home models because of the pandemic didn’t necessarily institute key security elements such as anti-malware, multi-level authentication, and endpoint protection.2 Now ransomware attacks are skyrocketing. As of 2021, more than 1/3 of organizations worldwide had experienced a ransomware attack or breach.3
To empower your hybrid workforce and protect your organization, you’ll need security awareness training, reliable cybersecurity policies, and the right solutions for the unique needs of your business.
How do you protect your business from a ransomware attack? The first step is understanding what it is and how it can get into your system. In our infographic, The anatomy of a ransomware attack, we help you understand this threat to your business so you can defend against it. It’s important to know:
1. How a ransomware attack begins
Cybercriminals search for networks that can be easily accessed. The size of the business doesn’t matter. All they need is for someone in a business to interact with one of their attack vectors so they can gain access to your network.
2. Common ransomware attack vectors
Ransomware can sneak into your network through a variety of attack vectors, including unsecured remote desktop protocol (RDP) connections, email phishing, email links, and software vulnerabilities due to expired security patches.
3. Define and identify a ransomware attack
Ransomware is malware that cybercriminals trick you into downloading. Once inside your network, ransomware encrypts your files, locking you out of your own system. Criminals hold your data and files hostage. If you pay the ransom, they give you the key to unlock the files. If you don’t … goodbye data.
4. Stages of a ransomware attack
Ransomware attacks vary, but they generally follow a pattern. Here are the basic stages.
- Campaign: The cybercriminal chooses the preferred method of attack, whether it’s weaponizing email, websites, or web servers.
- Infection: Malicious code starts to spread on the targeted network.
- Activation: The cybercriminal activates the attack.
- Encryption: Malware begins to encrypt data or files.
- Ransom request: Cybercriminal contacts the victim with instructions on how to pay the ransom via untraceable cryptocurrency such as Bitcoin.
- Recovery: The victim pays the ransom, which may or may not result in restoration of data and files.
- Cleanup: The organization’s cybersecurity team or consultant analyzes the attack, ensures that malware has been removed, and takes steps to prevent further attacks.
How can you prepare for ransomware attacks?
Your network and data can be vulnerable to a ransomware attack for a variety of reasons. You prepare by understanding if your network is cybersecure, holding your employees accountable to follow safety protocols, and having a plan in place for how to identify and respond to a ransomware attack. Because cyberthreats and the cybersecurity to defeat them is an ever-changing issue, having knowledgeable experts working as an extension of your team can help your business and your data stay protected.
The AT&T Cybersecurity Consulting team has a comprehensive portfolio of cybersecurity products as well as experts to help assess, evaluate, and recommend the right solutions.
Our team has been working with clients for over 25 years. Our consultants provide strategic advisory services for enterprises to plan and implement secure-by-design initiatives for networking, cloud, 5G, and IoT. We offer vulnerability and cyber risk assessment services to help customers attain cyber risk, compliance, and data privacy goals faster.
Our solutions can help you:
- Identify ransomware attacks
- Stop malware from gaining access to your network
- Detect and respond to threats before they impact your business
- Minimize the impact of a breach and enable analysis and recovery
We’re here to help.
At AT&T Business, we’re committed to making your business cybersecure. To learn more, download our infographic: “What is the anatomy of a ransomware attack?”
1C-Suite: Redesigning Work for a Hybrid Future, Gartner (2022): https://www.gartner.com/en/insights/seven-myths-about-hybrid-future-of-work
2The future of work within the professional services sector. Global Data (2021): https://www.business.att.com/content/dam/attbusiness/reports/the-future-of-work-within-the-professional-services-sector.pdf
3IDC Survey Finds More Than One Third of Organizations Worldwide Have Experienced a Ransomware Attack or Breach, IDC (August 2021): https://www.idc.com/getdoc.jsp?containerId=prUS48159121