Layered defense: Improving your network security
A layered defense that includes network security is an ideal way to address the rise in cyberattacks on businesses. A single security solution like a firewall simply cannot combat the savvy ways that cyber criminals can access your information. By combining a mix of overlapping security tools, policies, and best practices, you can better protect business systems from attack.
In 2023 the average cost of a data breach in the U.S. reached $9.48 million,1 with estimated total losses for all incidents exceeding $12.5 billion.2 However, one thing you won’t find in these numbers are the hidden costs due to operational disruption, reputational damage, insurance premium increases, or denials of coverage.3 While it’s difficult to quantify these costs in dollars, losing just a single customer because of a breach could impact your business for years. These damages can go beyond customer purchases to include the loss of referrals that customer may cost the business.
Why is layered defense needed to protect network traffic?
What are the principles behind layered defense and how do you build this into your business?
Layered defense is a network security strategy where multiple tactics are deployed across your network and its access points. The goal is to make sure that no single point of potential failure would give intruders access to your network. Layered defense supports a defense in depth strategy to create security redundancies. For this to work, you need to use a mix of overlapping security tools, policies, and best practices that cover the physical, administrative, and technical areas of your business. It’s important to note that layered defense is different from layered security, which deploys multiple products in a specific security area.
The role of a Zero Trust strategy in layered defense
With the ever-increasing frequency of cyberattacks, security professionals are seeking ways to cut down on the volume of malicious traffic. One way to do this is to treat every attempt to connect to the network with suspicion. Because cybercrime looks for opportunities to imitate authorized users, it can be difficult for even the savviest security with the latest protections to identify suspicious activity. For this reason, more companies are adopting a Zero Trust network access (ZTNA) approach to network traffic. In Zero Trust, traffic is examined before it reaches a firewall. All users are seen as threats until their identities can be verified using multifactor authentication tools, biometrics, or other verification methods.
The term “Zero Trust” was first coined by Forrester Research in 2010. Soon after, Google adopted the strategy in their network. Following Google’s best practice example, more companies have followed this “stop the traffic first, ask questions now” approach as an effective layered defense security strategy. It levels the playing field for all traffic, but also helps to take the strain off other tools by filtering out malicious traffic early. It’s especially important considering that many businesses have a network perimeter that isn’t clearly defined because of location, third-party visitors and applications, and other variables. Zero Trust is an advantage over relying solely on a traditional network firewall at the customer edge because it means users are verified no matter where they’re connecting from and what devices they’re using.
In the new era of remote and hybrid work, many employees access the business local area network (LAN) from home or use the public internet to connect to work servers, which can expose the network to vulnerabilities. It’s clear that this traffic needs to be treated with suspicion; however, in Zero Trust, employees accessing the network from the office are treated the same as authorized users who are connecting remotely. In the traditional model, traffic is then examined by a firewall where it is checked against security rules and policies to give you an additional layer of protection.
Improving your layered defense network security foundation
Zero Trust is a powerful, effective early step in your layered defense strategy. Because it’s effective, it has become an early layer of defense. But that’s after traffic has entered your network. The actual network itself is like the central nervous system of your business. As a result, it’s the first layer of your defense. Solutions like Zero Trust add to, integrate into, or collaborate with your network to create your security. However, now you can have some of those additional security tools built within it.
To address your need for a layered defense with security that starts with your network connectivity, we’ve developed network-embedded security that operates in-line with traffic. This service, called AT&T Dynamic Defense, is the first and only comprehensive security solution built into your network connectivity. It allows us to shift your network security foundation upstream away from the customer edge where our built-in security capabilities stop threats before they reach your business local area network (LAN).
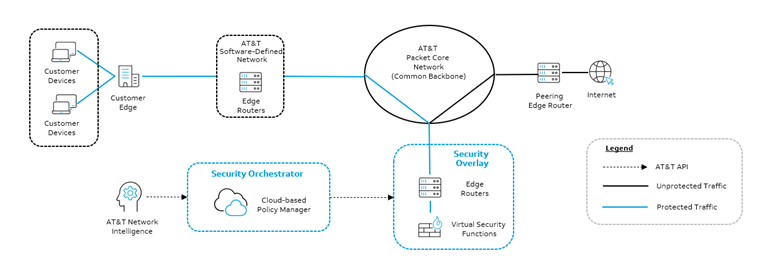
AT&T Dynamic Defense should be an essential element to your layered defense security strategy. AT&T Dynamic Defense Shield, embedded into your connectivity solution, uses AT&T’s threat intelligence libraries to dynamically blocks malicious IP addresses, identifying and filtering out malicious traffic before it reaches your network. This can lessen the burden on layered security tools like ZTNA before ZTNA needs to examine the traffic.
If you’d like a firewall within the network – that is, before tools like Zero Trust – you can add a NextGen stateful firewall with AT&T Dynamic Defense. It monitors and detects states of all traffic on the network to track and defend based on traffic patterns and flows.
And for even deeper, network-level defenses, you can add advanced threat protection to apply three types of threat protection profiles to security policies: virus protection, spyware protection, and vulnerability protection. Once additional to your core security, these are just a few of the active, yet future-ready features that can be activated as part of your network.
What does this mean for your IT team? Simplified security with fewer tools to maintain and update (the updates happen automatically at the network level, free resources for your business) and layered defense within your foundation for connectivity.
Adopting network security lightens the demand on your other traffic verification tools so they can better focus on the traffic they receive, potentially making your layered defense more efficient and effective. Less traffic also means your LAN can operate more efficiently, enabling approved business traffic to move more freely. In essence, this gives you “cleaner pipes.”

How open architecture is changing the way we innovate
Open innovation—open source software and open architecture technologies—is changing the network and how we collaborate in business.
Superior layered security starts with superior threat intelligence
In beta trials with our customers, AT&T matched an average of 20-25% of inbound network traffic to our threat intelligence libraries. This is an impressive number because it implies that up to 25% of the traffic on the internet intended for businesses is, at best, noise (ranging from harmless scans and pings to unknown sources) and at worst, potential attempts breach networks. Attempts that need to be identified and resolved.
Internet noise can be damaging because it clogs your network with unnecessary traffic that’ll need to be inspected by security tools like a firewall before it’s let through. In high-traffic environments, this can cause data transmission bottlenecks because a firewall has a limit as to how much data it can inspect in any given moment. If your network-embedded security solution can block this noise ahead of time, your downstream security tools will have less data to inspect, allowing rightful traffic to be transmitted more efficiently.
Clearly, it’s important to thwart breach attempts as early and efficiently as possible. AT&T maintains an extensive, ever-evolving list of threats and shields you against them. Once filtered out, any other layered security services, including Zero Trust, no longer have to deal with this potentially malicious traffic.
Considering that our global network carries over 710 petabytes of data traffic on an average day,4 which is the equivalent to streaming nearly 7.5 million 2-hour long 4K movies, we can understand what the threats are and how to quickly respond to them. The result is a network that is both better protected and operating more effectively.
Our libraries filter threats that include:
- Botnets
- Web scanners searching for web-facing vulnerabilities
- Virtual private networks (VPNs) that are flagged as suspicious
- Distributed Denial of Service (DDoS) attackers known for disrupting web or network traffic
- Malicious[MD5] actors identified via honeypots, which are tools used to lure likely bad actors with data they believe is valuable
In a separate trial with one of our customers (shown below), the combined power of AT&T Dynamic Defense and a third-party security tool flagged nearly half of inbound traffic flows as unwanted and potentially malicious—which is incredible. Once identified, this traffic was blocked before it reached the customer’s LAN, eliminating threats while allowing their network to operate more effectively.
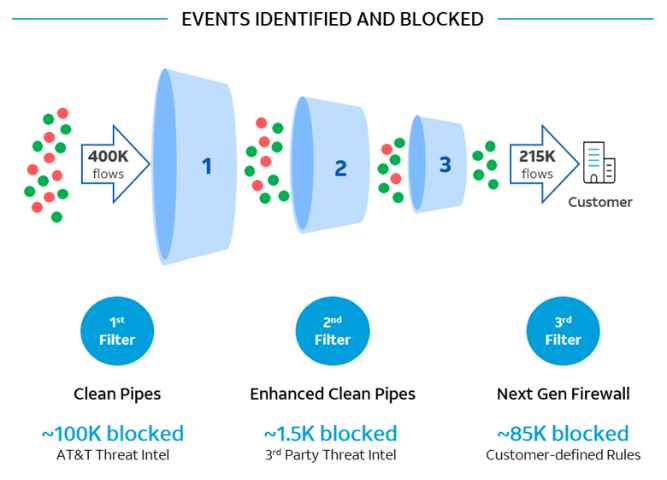
As illustrated, a layered security strategy can be very powerful. And, when you include in-network security that operates upstream from the business edge, you not only create foundational redundancy in the network layer, but you have traffic that has been vetted before it reaches the additional tools you have layered in the customer-defined rules in the illustration.
Next steps for your layered defense network security
Creating and adopting a layered security strategy can seem overwhelming. The cyber threat landscape changes as quickly as the technologies you choose for business operations. Reliability, simplicity, and effectiveness in your security solutions are the priorities of IT teams so they can protect the business.
Start by creating your own layered security strategy. Steps to consider are:
- Get a cybersecurity assessment to understand your security risks.
- Examine if you have cybersecurity best practices in place as part of your company culture.
- Develop a layered security plan that addresses the unique needs of your business.
- Create an action plan and timeline to implement your security plan.
As a leader in security technology with more than 1,000 security-related patents, our AT&T Chief Security Office detects and monitors an average of 180 billion security probes across our network each day. Our highly-trained security experts are always on the lookout for new threats to add to our extensive threat intelligence library. Intelligence we use to help protect both our network and yours. We’ve designed AT&T Dynamic Defense – the first and only comprehensive network security solution of its kind on the market – to deliver the reliability, simplicity, and effectiveness you need to protect your network.
But we’re not stopping there. We stay on top of several security-focused priorities simultaneously. These include but aren’t limited to 1) what our customers need, 2) monitoring and learning to stay ahead of the threat landscape, and 3) innovation that translates what we hear, learn, and anticipate into tested, effective solutions that address your pain points. Then, as we learn more, we evolve our solutions to continue to meet your needs.
Connecting changes everything. Connecting securely can make a big difference in how you operate and where you can focus, giving you more time to focus on how you service your customers.
Start building your layered defense strategy with security that starts at the network through AT&T Dynamic Defense. To connect with an expert who knows business, contact your AT&T Business representative.
Why AT&T Business?
See how ultra-fast, reliable fiber and 5G connectivity protected by built-in security give you a new level of confidence in the possibilities of your network. Let our experts work with you to solve your challenges and accelerate outcomes. Your business deserves the AT&T Business difference—a new standard for networking.
1“Cost of a Data Breach Report 2023,” IBM Security, 2023.
2“Federal Bureau of Investigation Internet Crime Report 2023,” FBI Internet Crime Complaint Center, 2023.
3“Seven hidden costs of a cyberattack,” Deloitte, Accessed April 12, 2024, https://www2.deloitte.com/us/en/pages/finance/articles/cfo-insights-seven-hidden-costs-cyberattack.html.


